AES Example - Round 1, Substitution Bytes current State Matrix is 0 B B @ 00 3C6E 47 1F 4E 22 74 0E 08 1B 31 54 59 0B1A 1 C C A substitute each entry (byte) of current state matrix by corresponding entry in AES S-Box for instance: byte 6E is substituted by entry of S-Box in row 6 and column E, i.e., by 9F this leads to new State Matrix 0 B B. Generate symmetric key using AES-128. Generate initialization vector used for CBC (Cipher Block Chaining). Encrypt message using symmetric key and initialization vector. Decrypt the encrypted message using symmetric key and initialization vector. The AES algorithm has a 128-bit block size, regardless of whether you key length is 256, 192 or 128 bits. When a symmetric cipher mode requires an IV, the length of the IV must be equal to the block size of the cipher. Hence, you must always use an IV of 128 bits (16 bytes) with AES. $ openssl genpkey -algorithm RSA -aes-128-cbc -out key.pem. The passphrase can also be specified non-interactively: $ openssl genpkey -algorithm RSA -aes-128-cbc -pass pass: -out key.pem. Cool Tip: Check the quality of your SSL certificate! Find out its Key length from the Linux command line!
To encrypt data with AES, you need a key. If you are not familiar with key generation, please check out How to generate an AES key for more information.
Note: Please understand that only encrypting data with AES-CBC does not keep the data safe from modification or viewing. You still have to protect the key from others and the integrity of the data. This article only shows you how to use the AES API to encrypt some data with the AES-CBC mode.
To start using AES, add the header file for the module to your file:
Declare the variables needed for AES encryption:
This examples assumes you've filled the variable named key with the 32 bytes of the AES key (see How to generate an AES key), iv with 16 bytes of random data for use as the Initialization Vector (IV) and input with 40 bytes of input data, and zeroized the rest of input.
The CBC mode for AES assumes that you provide data in blocks of 16 bytes. Because there are only 40 bytes of data, you have to extend the input to contain 48 bytes of data, instead. There are multiple ways to pad input data. One is to add zeroes to the end. This is only secure if you also transmit the original length of the input data (40 in this case) securely to the other side, as well. This example uses padding with zeroes.
128 Bit Aes Key Generator
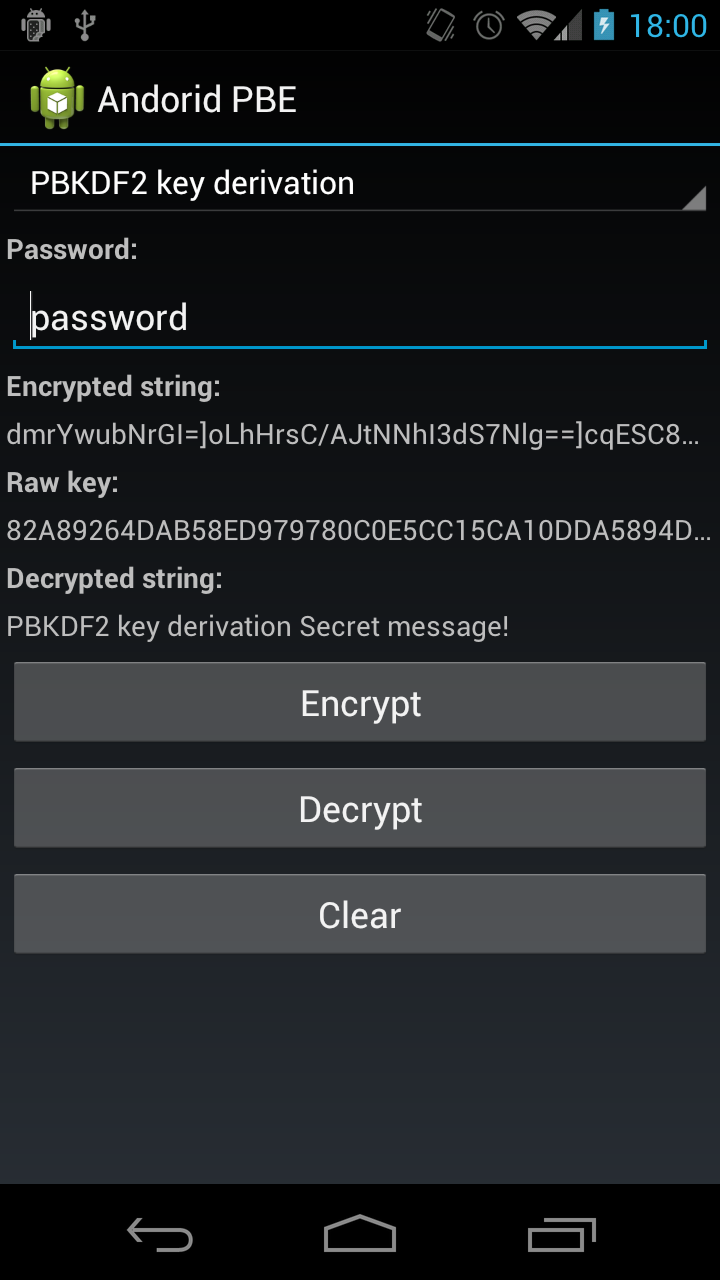
Aes 128 Cbc Key Generator Manual
First, initialize the AES context with your key, and then encrypt the data (with padding) to the output buffer with your iv:
Aes 128 Cbc Key Generator Download
The first 48 bytes of the output buffer contain the encrypted data. This data is only protected for confidentiality purposes. You need to send the length of the input data, the IV and the output buffer to the other side while protecting the integrity of those values. In addition, the other side needs the key without anybody ever knowing it. Usually this means making a hash over the length of the input data, the IV and the output buffer and encrypting this hash and the AES key with the public RSA key of the other party using the PKCS#1 encrypt function.